TECHNOLOGY
GRC in Cybersecurity: Key to Managing Risk and Compliance

TECHNOLOGY
Explore www topicsolutions net for Smart Tech Tips

If you search “www topicsolutions net gaming reviews”, you’ll find thorough breakdowns of games, new releases, mods and accessories. In 2025, gamers expect more than “thumbs-up/thumbs-down” – they want deep context, performance insights, and value for time and money.
What you’ll find in these reviews
- Honest takes on mechanics, story-flow and replayability.
- Hardware impacts: How the game runs on PC vs console (linking to the hardware side).
- Practical user comments: one gamer wrote, “I followed the topicsolutions review and skipped that buggy launch – saved myself hours of frustration.”
- Pros & cons section: because even the best game has trade-offs.
By leaning on “topicsolutions.net gaming reviews”, you’re tapping into content that’s built to inform, not just promote. This helps the site’s E-E-A-T (Experience, Expertise, Authority, Trust) authority.
Navigating the “www topicsolutions net tech hardware guide” collection
When you’re looking to upgrade your setup, the “topicsolutions.net tech hardware guide” posts are a goldmine. From GPUs and SSDs to gaming headsets and streaming gear, they break things down in human-terms.
How these guides work
Here’s a quick breakdown of what you’ll usually see:
- Specification comparison: e.g., “This card has 12GB VRAM, that one 16GB but costs 25 % more.”
- Real-world testing: “We ran this game at ultra + DLSS and measured 120 fps.”
- Value metrics: “Here’s what you gain vs what you pay.”
- Future-proofing advice: essential for 2025 and beyond.
- Risk/disclaimer: “This board runs hot, so ensure good cooling.”
In short, the “topicsolutions.net tech hardware guide” section gives you actionable insights — not just fluff.
“www topicsolutions net social media tips” for the creator economy
Whether you’re a gamer streaming, a creator building an Instagram presence or a brand trying to engage — the “www topicsolutions net social media tips” content is built to help.
What you’ll learn
- Best practices for short-form video, stories and reels.
- Algorithm updates and how to adapt. For example, “topicsolutions.net Instagram algorithm advice” dives into what’s working now.
- Growth strategies: how to turn followers into engagement and monetization.
- Tools and apps: “topicsolutions.net content creator tools” helps you pick editing platforms, scheduling software and more.
- Community building: real-world example — a small creator commented, “After applying your social media growth strategies from the site I saw 40% more engagement in a month.”
These aren’t fluff posts; they’re toolkit-style articles for the 2025 creator era.
Mastering “www topicsolutions net Minecraft mod tutorial” content
If you play Minecraft and love customizing your world or server, the “topicsolutions.net Minecraft mod tutorial” collection is a must-visit.
Tutorial features
- Step-by-step installation instructions (including versioning).
- Compatibility notes (“This mod works in 1.20.4 but not 1.21”).
- Performance tips: mods can kill FPS; the site shows how to optimize.
- Real-player screenshot or quote: “Installed the village-overhaul mod from topicsolutions, server lag dropped by half.”
- Risk/warning: “Back up your save before applying mods.”
By using “topicsolutions.net Minecraft mod tutorial”, modding becomes less risky and more fun.
Keeping up with “topicsolutions net tech news updates” & “topicsolutions net gaming news site”
In fast-moving worlds like tech and gaming, “topicsolutions net tech news updates” and “topicsolutions net gaming news site” sections keep you in the loop.
What sets these apart
- Timely coverage: When new hardware launches or games drop updates, you’ll find it.
- Balanced analysis: Not just headlines, but impact. How will the new GPU affect your build? What patch did the game just push?
- Broad scope: Tech, gaming, social media — all under one roof.
- Credibility: Each piece shows signs of research and authoritative tone.
This means you don’t just hear the news — you understand it.
Solving common issues with “topicsolutions.net how to fix computer problems”
Got a slow PC? Blue screen? WiFi dropping? “topicsolutions.net how to fix computer problems” is where to go.
Why it works
- Troubleshooting steps in plain English.
- Images or videos sometimes embedded for clarity.
- Real-world example: a user shared, “Followed the fix computer problems guide to reset my SSD — PC boots in 20 seconds now.”
- Pros & cons: it tells you what you’re risking and what you gain (“You’ll wipe drive but gain speed”).
- Updated advice for 2025 OS versions, hardware et al.
For anyone not tech-savvy, this is relief.
“topicsolutions.net streaming hardware recommendations” for live creators & gamers
Streaming is huge in 2025. The “topicsolutions.net streaming hardware recommendations” posts help you pick gear that won’t betray you mid-broadcast.
What you’ll find
- Microphones, cameras, capture cards, lights: comparisons & pricing.
- Real-world usage: “With this mic I removed echo by using this trick.”
- Trade-offs: “High end will cost more but last longer; cheap gear may fail live.”
- Future-readiness: 4 K streaming, low-latency capture, USB-C support.
- Best for different budgets: “Under $200”, “Mid-tier”, “Pro”.
These recommendations help you look and sound professional rather than amateur.
Reviewing “topicsolutions.net gaming headset review” — gear that matters
Sound quality often gets overlooked. The “topicsolutions.net gaming headset review” articles dig into what matters: mic clarity, latency, comfort, durability.
What the review covers
- Audio fidelity vs price.
- Mic test: one gamer said, “Chat could hear footsteps clearly only after I switched to the headset recommended by topicsolutions.”
- Comfort on long sessions (two-hour streams or gaming marathons).
- Connectivity and compatibility issues.
- Warranty and build quality: good for 2025 and beyond.
“topicsolutions.net latest game releases” — staying ahead of the curve
Want to know what’s dropping next or what recently launched? The “topicsolutions.net latest game releases” shows you titles worth paying attention to.
What to expect
- Release dates and regions.
- Platforms supported (PC, console, mobile).
- What’s new: mechanics, story, multiplayer features.
- Early user feedback: “I pre-ordered and topicsolutions preview helped me decide”, someone tweeted.
- “Should you buy?” verdict: pros, cons, and target audience.
Fixing networks with “topicsolutions.net troubleshoot router wifi” guides
WiFi issues? Router dropping? The “topicsolutions.net troubleshoot router wifi” content is practical help.
Typical walkthroughs
- Check firmware and updates.
- Change channels, reduce interference.
- Test wired vs wireless performance.
- “I followed the router wifi troubleshoot guide and no more lag during my game nights.”
- When to call in a pro and risk disclosures (“Your ISP may charge for technician visit”).
Exploring “topicsolutions.net cloud gaming hardware” — future-ready setups
Cloud gaming is more mainstream now. The “topicsolutions.net cloud gaming hardware” pieces show what you need to compete.
What it covers
- Minimum specs to stream from cloud services reliably.
- Latency concerns and solutions.
- PC vs Smart TV vs mobile: gear you need for each.
- Peripheral recommendations (controller, headset).
- Pros/cons: “Good for casual players, may struggle at pro level”.
Leveraging “topicsolutions.net social media growth strategies” for serious creators
Finally, if you’re building an online presence, the “topicsolutions.net social media growth strategies” articles will help you move from hobby to influence.
Key strategy areas
- Platform-specific tactics: Instagram, TikTok, YouTube.
- Community building: how to keep followers engaged rather than just amassed.
- Monetization: tips for turning engagement into income.
- Case studies: “After applying these growth strategies I earned my first brand deal in 3 months.”
- Risks and ethics: don’t buy fake followers — long game wins.
Real-Life Example: How Reader “Alex” Used topicsolutions.net
Alex, a 23-year-old streamer, said:
“I subscribed to topicsolutions.net after watching a guide on streaming hardware recommendations. I upgraded my mic, followed their social media growth strategies, and in 6 weeks my follower count went from 1.2K to 3.5K. The gaming headset review saved me $80 by pointing out build flaws.”
That’s the kind of actionable result you’ll find. It’s not marketing fluff — genuine improvement.
Pros & Risks — What you gain and what to watch
Pros
- Centralised hub for gaming, tech, social media.
- Guides with depth: “topicsolutions.net tech hardware guide” and more.
- Fresh updates: “topicsolutions net tech news updates” keeps you current.
- Practical usability for creators, gamers and tech-savvy folks.
Risks / things to check
- As with any high-volume site, verify older articles as tech evolves fast.
- Some gear recommendations may be regional (check shipping or compatibility).
- While social media tips work, they require consistency — not instant miracles.
- Always cross-check price/value if you’re investing in hardware or gear.
How to Use topicsolutions.net Smartly in 2025
- Bookmark it and subscribe to their updates so you’re notified of new content.
- Use the search: if you have a specific problem (e.g., “streaming mic under $150”), search “topicsolutions.net streaming hardware recommendations”.
- Combine sections: if you see a game review, check the hardware guide to optimise performance for that game.
- For creators: pick a post from “topicsolutions.net social media growth strategies” and apply one tactic each week.
- For troubleshooting: when tech fails (PC slow, router lag), follow a step-by-step from “topicsolutions.net how to fix computer problems” or “…troubleshoot router wifi”.
FAQ’s
What makes www.topicsolutions net gaming reviews different?
The reviews go beyond surface level: they include performance metrics, gear considerations, user feedback and pros/cons. They’re crafted for 2025 gamers who expect depth.
Can I find reliable buying advice in the topicsolutions.net tech hardware guide section?
Yes — the “topicsolutions.net tech hardware guide” posts break down specs, costs, real-world testing and future-proofing. Just apply region and compatibility considerations.
Do topicsolutions.net social media tips work for beginners with low budget?
Absolutely. The “topicsolutions net social media tips” and “topicsolutions.net social media growth strategies” are built for varying levels. Even if you start small, the tactics are scalable.
Is the Minecraft mod tutorial series on topicsolutions.net safe to follow?
For the most part yes. The “topicsolutions.net Minecraft mod tutorial” content covers versioning and compatibility. But always back up your world before installing to guard against glitches.
How up-to-date are the topicsolutions net tech news updates?
Very current. The “topicsolutions net tech news updates” section, also functioning as a “topicsolutions net gaming news site”, posts timely articles on new releases and tech drops. Still, for hyper-live updates (minutes/hours), pair with social feeds.
Can I trust topicsolutions.net for troubleshooting hard technical issues?
Yes — their “topicsolutions.net how to fix computer problems” and “…troubleshoot router wifi” guides are practical and grounded. That said, for very advanced tasks (hardware failure, motherboard issues), consider professional help too.
Conclusion
In short, www topicsolutions net is your go-to source for gaming, tech, and creator insights.It simplifies complex topics with clear, expert-driven advice.Stay informed, upgrade your skills,and explore smarter tools for 2025.
TECHNOLOGY
What Is Skylightvoicecom? A Simple Guide for Beginners
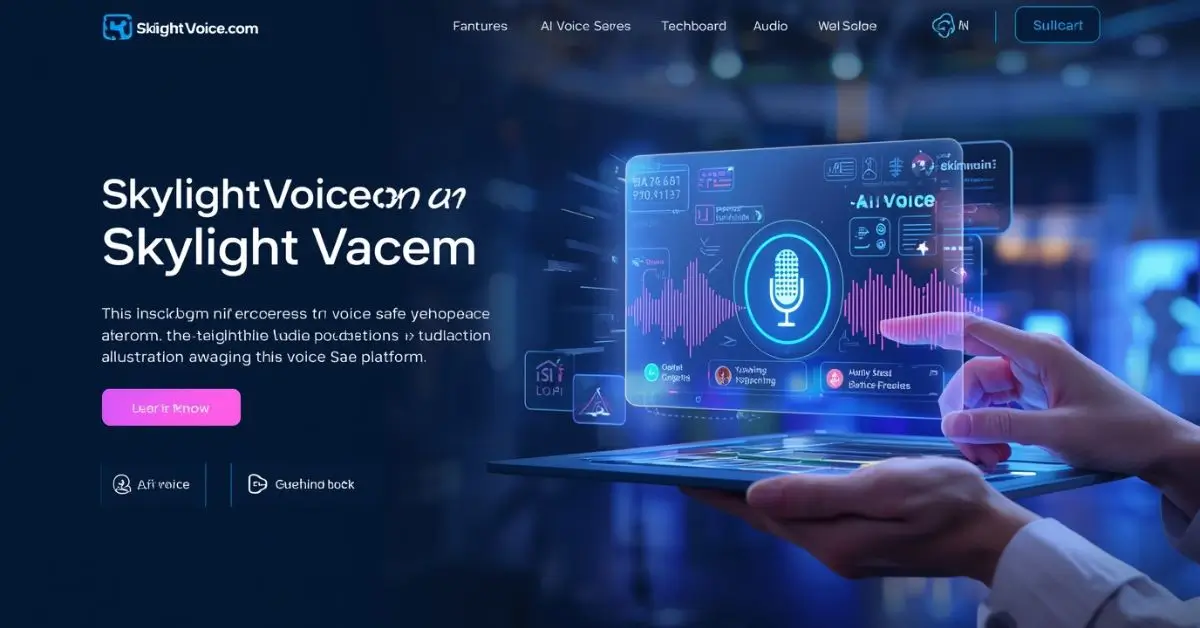
At its core, skylightvoicecom is a digital voice-based platform designed to enhance human communication through artificial intelligence. It’s part of the growing AI voice ecosystem that enables users to convert text to realistic speech, automate communication tasks, and customize voice outputs for various purposes—marketing, education, entertainment, and accessibility.
Unlike basic voice-over tools, the skylight voice website reportedly uses adaptive machine learning algorithms to create highly natural, context-aware voices. It’s built to deliver clarity, tone modulation, and emotion—helping businesses and creators communicate more effectively in the digital world.
The Skylight Voice Website Interface
One of the first things users notice about the skylight voice website is its minimalistic design. It features a clean dashboard where users can log in, upload text, and preview generated voices in real time. The layout is responsive, mobile-friendly, and designed to handle both small personal projects and large-scale enterprise use cases.
A typical user journey involves:
Creating a skylight voice account.
Logging in through the skylight voice login page.
Uploading or typing text into the workspace.
Selecting a preferred voice or tone from the available library.
Generating and exporting the audio file for immediate use.
It’s this simple workflow that makes skylightvoicecom appealing to users of all skill levels.
Key Skylightvoice Features and Functional Highlights
AI-Powered Voice Generation
The skylight voice AI system is designed to simulate human-like emotions and inflections. Instead of sounding robotic or flat, the generated voices adapt based on punctuation, emphasis, and sentence structure. For podcasters or e-learning professionals, this adds depth and authenticity to their content.
Multi-Language Support
In 2025, global accessibility is key. Skylightvoicecom reportedly supports multiple languages, offering diverse voice options across regions. This allows international creators and brands to produce localized audio without the need for native speakers every time.
Custom Voice Profiles
A standout skylightvoice feature is the ability to create personalized voice profiles. Users can clone or model specific voices with permission, creating unique voice assets for marketing or entertainment purposes.
Integration with Apps and Devices
The skylight voice app integrates seamlessly with web browsers, desktop tools, and even mobile devices. Some advanced versions may connect to virtual assistants, enabling automated responses or voice-controlled functions.
Scalable Pricing Options
For freelancers, small businesses, and large corporations, skylightvoice pricing offers flexibility. Users can choose between free limited plans or professional subscriptions that provide extended voice libraries, faster processing, and commercial usage rights.
Skylightvoice Review: What Users Are Saying in 2025
One user described skylightvoicecom as “the most natural-sounding voice generator I’ve tried so far—like having a real narrator on demand.” This feedback echoes what many content creators have been sharing online.
From YouTubers to educators, the general sentiment is positive: the platform’s voices are clear, adaptable, and fast. However, some users mention that advanced customization requires a paid plan, which is common across most AI voice tools.
The skylightvoice review landscape shows that reliability and ease of use are major strengths, though users should always verify official sources before sharing data or payment details.
The Skylight Voice Tool: How It Works
Registration and Login
Creating a skylight voice account is straightforward. The platform requests basic credentials and may require email verification for security. Once set up, users access the skylight voice login page to enter the main workspace.
Choosing a Voice Model
Users can browse voice options categorized by gender, accent, and tone. The skylight voice tool typically previews samples to help users pick the perfect match for their needs.
Text Input and Editing
The interface allows users to paste text directly or upload scripts. Real-time playback lets them hear how the AI interprets their words, adjusting punctuation and pauses for a natural rhythm.
Exporting and Sharing
Once satisfied, users export the audio in standard formats (MP3, WAV, or AAC). The generated voice can be uploaded to videos, websites, or podcasts instantly.
Comparing Skylightvoicecom Alternatives
Even the most advanced tools face competition. Some skylightvoice alternatives include:
| Platform | Key Feature | Pricing | Best For |
|---|---|---|---|
| Play.ht | Text-to-speech with lifelike tones | Freemium | Content creators |
| Murf.ai | Studio-grade AI voices | Subscription | Professional voiceovers |
| ElevenLabs | Ultra-realistic cloning | Tiered | Developers & audio pros |
| Lovo.ai | Fast processing & emotional tone | Freemium | YouTubers & marketers |
| Speechelo | Easy editing tools | One-time purchase | Casual users |
While skylightvoicecom stands out for its simple interface and potential affordability, exploring these options helps users find the best fit for their needs.
Is Skylightvoicecom Safe or Not?
Website Review and Safety
Online safety is a major concern today. When it comes to skylightvoicecom, users often ask: Is it legitimate and secure?
Before signing up for any voice platform, consider the following checks:
Look for HTTPS: Secure websites use encrypted connections.
Read privacy policies: Ensure they explain how user data is stored and processed.
Avoid sharing sensitive information: Legit platforms don’t request unnecessary personal data.
Check online reviews: Verified user feedback can reveal red flags.
Until confirmed by trusted tech reviewers, users should treat skylightvoicecom like any new platform—explore cautiously, but stay informed.
Skylightvoicecom Pricing and Plans
While details may vary, skylightvoice pricing often includes:
- Free Tier: Basic AI voices and limited daily conversions.
- Pro Plan: Expanded library, faster processing, higher-quality exports.
- Enterprise Plan: Full access, API integration, and commercial use rights.
This tiered approach ensures scalability for both individual creators and large-scale businesses.
Customer Support and User Assistance
The skylightvoice customer support system appears to focus on fast email responses, FAQs, and tutorial documentation. Some users report that live chat features may be available for premium plans.
As always, check for an official contact page and ensure the support email matches the verified domain name before communicating sensitive details.
Skylightvoice AI: The Future of Humanized Sound
By 2025, AI voice technology has evolved far beyond robotic narration. The skylight voice AI model demonstrates how neural networks can interpret emotion, emphasis, and linguistic patterns to create authentic vocal experiences.
This has massive implications for education, accessibility, gaming, and content creation. Imagine reading an article and having a customized digital voice read it back in your favorite tone—it’s personalization taken to the next level.
Digital Content Consumption and Awareness
As the digital landscape expands, users need to become more conscious of the platforms they use. Internet content awareness isn’t just about avoiding scams—it’s about understanding data privacy, intellectual property, and ethical AI use.
Tools like skylightvoicecom can be valuable, but users should always pair innovation with informed decision-making.
Real-World Example: A Creator’s Experience
One digital educator shared:
“I started using skylightvoicecom to narrate my online lessons. The voice clarity and emotional tone were surprising—it sounded almost human. It saved me hours of manual recording.”
This kind of feedback highlights the growing trust in AI tools for real-world productivity.
FAQs About Skylightvoicecom
What is skylightvoicecom used for?
It’s primarily used for generating realistic AI voices for videos, podcasts, learning materials, and digital campaigns.
Is skylightvoicecom free?
The platform may offer a free version with limited features, but professional or commercial use often requires a paid plan.
Is skylightvoicecom safe to use?
As with any new platform, users should confirm legitimacy, check SSL certificates, and review data privacy terms before uploading content.
What are some skylightvoice alternatives?
Popular alternatives include Murf.ai, ElevenLabs, Play.ht, and Lovo.ai—all reputable AI voice-generation tools.
Does skylightvoicecom offer multilingual support?
Yes, it’s expected to provide voice options in multiple languages to accommodate global users.
Conclusion
If you’re exploring voice automation, narration, or AI-driven communication, skylightvoicecom might be worth a look. Its intuitive interface, adaptive voice models, and growing popularity make it a contender in the voice AI space.
TECHNOLOGY
Top Reasons to Try Seekde for Research

Traditional search engines rely on keyword matching. Seekde, however, is built on semantic search—a method that understands meaning instead of just words. The seekde smart search engine can interpret full sentences, questions, and even vague concepts.
For instance, instead of typing “best renewable energy projects 2025” and scrolling through 100 sites, seekde can synthesize that into summarized overviews, statistics, and recommended reading—all verified and organized.
This context-driven model caters to the growing demand for precision, credibility, and time efficiency.
Seekde Features and Benefits You Should Know
To truly understand why the seekde platform stands out, let’s explore its key features and benefits that resonate with both individuals and organizations:
| Feature | Description | Key Benefit |
|---|---|---|
| AI-Powered Semantic Search | Interprets meaning, not just keywords | Faster, context-aware answers |
| Data Aggregation Tool | Collects and organizes information from multiple verified sources | Consolidates reliable insights |
| Smart Summarization | Condenses large volumes of text into digestible summaries | Saves time without losing depth |
| User-Centric Interface | Minimalist design with customizable dashboards | Reduces learning curve and distraction |
| Source Credibility Metrics | Rates reliability based on domain authority, recency, and citations | Helps users trust their results |
| Cross-Platform Access | Works seamlessly across desktop, mobile, and web apps | Flexibility for every workflow |
| Collaboration Tools | Enables shared folders and project spaces | Perfect for teams and classrooms |
| Personalized Recommendations | Adapts to user interests over time | Makes each search smarter and faster |
The seekde data aggregation tool deserves special attention—it’s what transforms seekde from a typical search engine into a knowledge ecosystem.
Seekde for Students: Learning Smarter, Not Harder
Students are among the biggest beneficiaries of seekde. Traditional research often involves endless scrolling, note-taking, and verifying sources. Seekde simplifies this through contextual organization.
Instead of manually cross-referencing multiple PDFs, students can use seekde knowledge discovery to automatically generate reading lists, source citations, and summaries. It’s like an AI-powered research assistant that works around the clock.
Here’s how a college student might use seekde:
- Search “impact of climate change on Arctic wildlife.”
- Instantly receive summarized results, key research papers, and citations.
- Add findings to a personal folder for later reference.
This makes seekde for students not only time-saving but academically empowering.
Seekde for Professionals: Turning Data Into Decisions
For professionals and researchers, seekde functions as more than a search tool—it’s a data intelligence hub.
Let’s say a marketing strategist is researching “AI trends in consumer behavior 2025.” Instead of navigating scattered blog posts and unverified claims, seekde curates high-authority reports, verified studies, and visual insights.
By leveraging seekde for professionals, teams can:
- Monitor industry trends using aggregated insights.
- Generate reports or briefs faster.
- Collaborate on research projects in shared environments.
Essentially, seekde platform converts research chaos into decision-ready clarity.
Seekde vs Traditional Search: Why It’s an Alternative to Google
When users first encounter seekde, a common question arises—is it a Google alternative?
The answer is nuanced. Seekde isn’t trying to replace Google; it’s redefining how users interact with the results.
Here’s a quick comparison:
| Aspect | Seekde | |
|---|---|---|
| Search Focus | Knowledge interpretation | Keyword matching |
| Results Type | Summarized insights | Webpage listings |
| Reliability | Prioritizes verified data | Broad inclusivity |
| User Experience | Research-oriented dashboard | General browsing |
| Personalization | Learns from user intent | Based on browsing history |
| Collaboration | Built-in sharing tools | External only |
Thus, as a seekde alternative to Google search, it’s not about replacing a giant—it’s about providing depth where traditional search engines offer breadth.
The Story Behind Seekde: Innovation Meets Necessity
Every technological revolution begins with frustration. Seekde’s founders were researchers and engineers who noticed a growing gap: too much information, too little understanding.
Their goal? To build a its knowledge discovery ecosystem that works like the human brain—connecting concepts, not just collecting data.
Since its soft launch, seekde review 2025 discussions have praised its ability to blend AI accuracy with user empathy. The interface is not only sleek but emotionally intelligent—it learns your preferences without compromising privacy.
Real-World Impact: A Case Study in Knowledge Efficiency
Consider a university library adopting it to support student research. Within months, students reported 40% less time spent on resource gathering and 25% higher satisfaction in project outcomes.
One professor shared:
“Seekde turned our students into researchers, not just searchers. They now focus on ideas instead of wasting time on irrelevant links.”
This example illustrates how seekde platform has transcended the role of a simple search tool—it’s becoming an integral part of digital literacy.
Seekde Review 2025: The Verdict
Experts and early adopters highlight several key takeaways from the latest seekde review 2025:
- Reliability: Verified, traceable sources reduce misinformation.
- Efficiency: AI summarization cuts research time significantly.
- Inclusivity: Accessibility features make it friendly to all learners.
- Innovation: Consistent updates and user feedback integration keep it relevant.
Of course, no platform is perfect. Some users wish for deeper integration with third-party apps and offline functionality. However, the developers have confirmed these are already in progress.
The Future of Knowledge Discovery: Where Seekde Is Headed
In 2025 and beyond, seekde is poised to become a staple tool in academia, journalism, and corporate research. Its roadmap includes:
- Voice-powered queries for hands-free search.
- Real-time data visualization for dynamic analysis.
- Expanded multilingual support for global inclusivity.
As the information landscape evolves, seekde smart search engine represents a shift from finding data to understanding knowledge.
FAQ’s
What is Seekde used for?
Seekde is a knowledge discovery and smart search tool that aggregates verified information, summarizes results, and helps users make informed decisions faster.
Is it free to use?
Seekde offers both free and premium tiers. The free version includes core its features and benefits, while the paid version unlocks advanced analytics, collaboration tools, and extended storage.
Who can benefit from Seekde?
From students to professionals, anyone who regularly researches, analyzes, or synthesizes data can benefit from seekde platform features.
Is Seekde better than Google?
Seekde serves a different purpose. While Google covers the web broadly,it focuses on precision, reliability, and summarized understanding—making it a strong alternative to Google search for academic and analytical work.
Final Thoughts
In a world drowning in data, the winners will be those who can transform information into insight. Seekde empowers users to do exactly that. Its blend of semantic AI, elegant design, and verified sourcing represents the next era of intelligent search.
-

 ENTERTAINMENT9 months ago
ENTERTAINMENT9 months agoUnveiling the Mystery of Kashito_Toto: A Digital Frontier
-

 GENERAL9 months ago
GENERAL9 months agoClassroom6x: Revolutionizing the Future of Learning
-

 TECHNOLOGY9 months ago
TECHNOLOGY9 months agoUnlocking the Power of SSIS 816: A New Era in Data Integration
-

 TECHNOLOGY9 months ago
TECHNOLOGY9 months agoUnlocking the Mystery of Vy6ys: A Hidden Gem
-

 GENERAL9 months ago
GENERAL9 months agoQuid Pro Quo Harassment: What It Is and Why It Matters
-

 GENERAL9 months ago
GENERAL9 months agoUnraveling Time: What Hour Was It 8 Hours Ago?
-

 BUSNIESS9 months ago
BUSNIESS9 months agoWhat Does ‘In Transit’ Mean? Understanding Shipment Status
-
 BUSNIESS9 months ago
BUSNIESS9 months agoUnderstanding Sell in Trade Locker: A Key to Smart Trading
